The return of the Linux router... (from pfSense to Debian, part 5: Enabling VoIP)
Hi again world ... two months without writing a single article... my notes are piling up ... no holidays, commited to my CFGS final project, now CCNP Route joins the party ... I really need a breathe...
But here we are!!!
Today I'm going to share a very short one! but one that proved to be a vast enhancement when comparing with the old days of pfSense... VoIP!
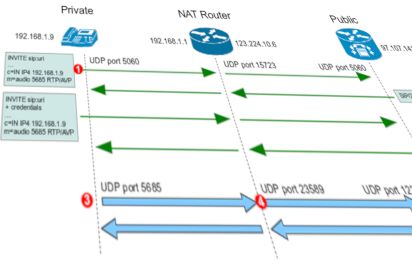
NAT on pfSense when handling SIP protocols was a nightmare, and often, the sure way to not getting trouble with VoIP was to have voice VLAN directly connected to gateway, bypassing firewall...
But now, with my beloved Debian routers, everything runs as it should.
SIP seems to be tricky on its own, in fact, to make it to work perfectly in my Debian / ipTables based firewalls, it turned out that some specific kernel modules have to be loaded to perform the magic.
What really shocked me is that pfSense, a corporative firewall meant to be managed from a GUI didn't had it solved.
My guess is that, probably, a BSD expert could load equivalen kernel modules for pfSense (provide that the base BSD packages for such modules do exist)... but anyhow... who cares... here's the piece of magic on Debian Linux:
modprobe nf_nat_sip nf_conntrack_sip
modprobe nf_conntrack_h323 nf_conntrack_h323
modprobe nf_conntrack_sip
modprobe nf_conntrack_sip ports=5060
You may want to put this on /etc/modules file, to make then to load on boot.
Just with four commands, an I got plenty of VoIP terminals, registered to cloud SIP providers without a single issue or conflict.
Of course, iptables has to be configured to allow traffic flow from VoIP protocols, but the troublesome part, NAT, is now solved.
Here are just four lines to help point on what is needed on an iptables setup to make SIP VoIP to flow.
Note this is not a complete setup, but just the very minimal to allow SIP VoIP...
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A INPUT -p udp --dport 5060 -j ACCEPT
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A FORWARD -p udp -j ACCEPT
iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A OUTPUT -p udp -j ACCEPT
Well... Enough for tonight...
Happy networking!!!
